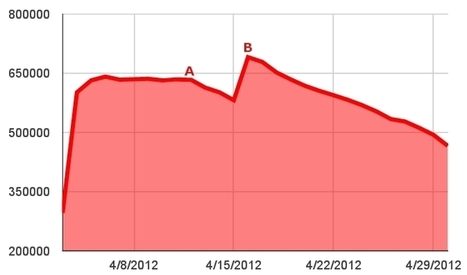
Dr. Web's count of Macs actively infected with Flashback over time. The "A" marks Apple's release of its Flashback removal tool, and the "B" marks Dr. Web's discovery of another variant of Flashback that led to an increase in its infection count.
===> Flashback has been used for click fraud, as detailed by Symantec’s researchers. The malware redirected traffic from Google search ads to its own pay-per-click ads, generating as much as $10,000 a day. <===
Even with its command and control servers disabled, the infected machines continue to engage in that traffic-hijacking. And with nearly half a million users still infected, Flashback’s authors are still likely profiting from their scheme.
Read more...



 Your new post is loading...
Your new post is loading...