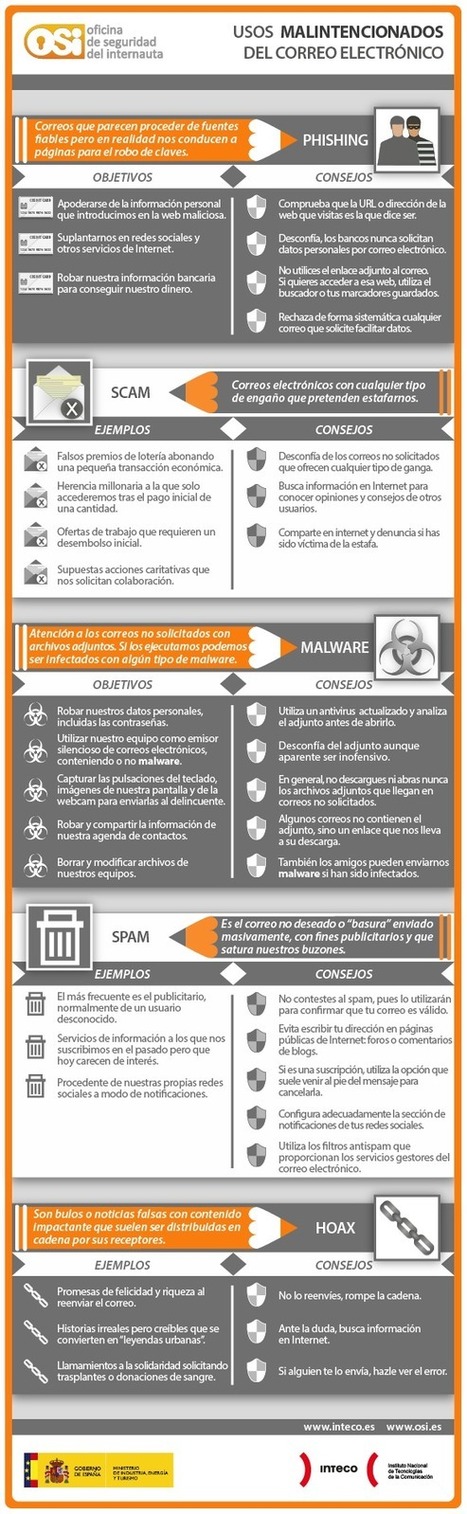
Muchos usuarios de Windows consideran que cuando el ordenador no les está funcionando de forma correcta es que se han visto infectados por un virus. Este nombre lo usan para describir cualquier tipo de mal comportamiento que se presente mientras se usa el sistema operativo. En muchos casos tampoco saben que existen varios tipos de infecciones: spyware, adware, gusanos o troyanos. Todos tienen sus propias características y afectan a la PC de manera distinta.
Via Gumersindo Fernández



 Your new post is loading...
Your new post is loading...







![H1 2014 Threat Report - F-Secure [Infographic] | Education 2.0 & 3.0 | Scoop.it](https://img.scoop.it/3WKggSg7n-Fjl4tKZAeUKDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)




